Enabling Password Based Authentication by Default for Snapshots
Enabling Password Based Authentication for SSH is simple way to connect to a system or instance via a username and password. Public Key Authentication is more secure due to the cryptographic algorithms that are commonly used to produce a key pair. However, if Password Based Authentication fits your use case then the following article could be relevant for you!
WARNING
Allowing Password Based Authentication via SSH is a major security risk. I am not responsible for any abuse that occurs by enabling this feature.
Configuration
The instances in this article were created in AWS. At the time of writing this I am using an Amazon Provided Red Hat 9 AMI in the eu-west-1 region, ami-0f2cb8c8044faf2da.
Enable Password Based Authentication
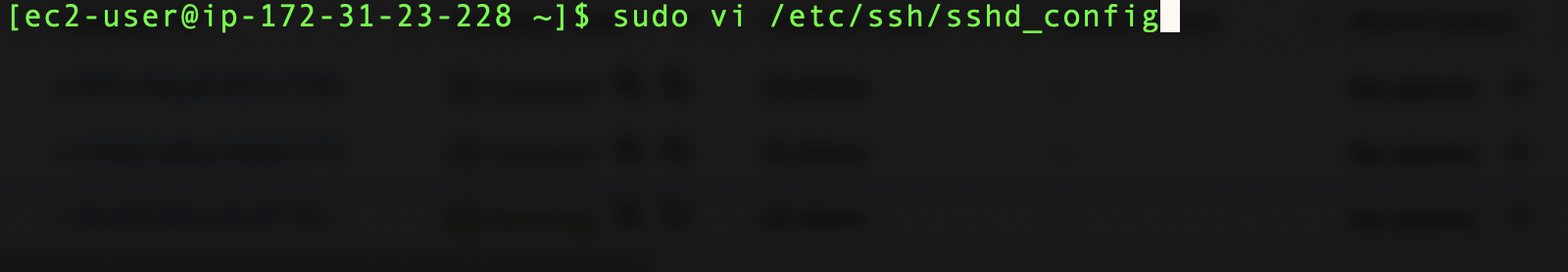
Start by editing the sshd_config file, which can be found in the /etc/ssh directory. You will have to perform this command as root.
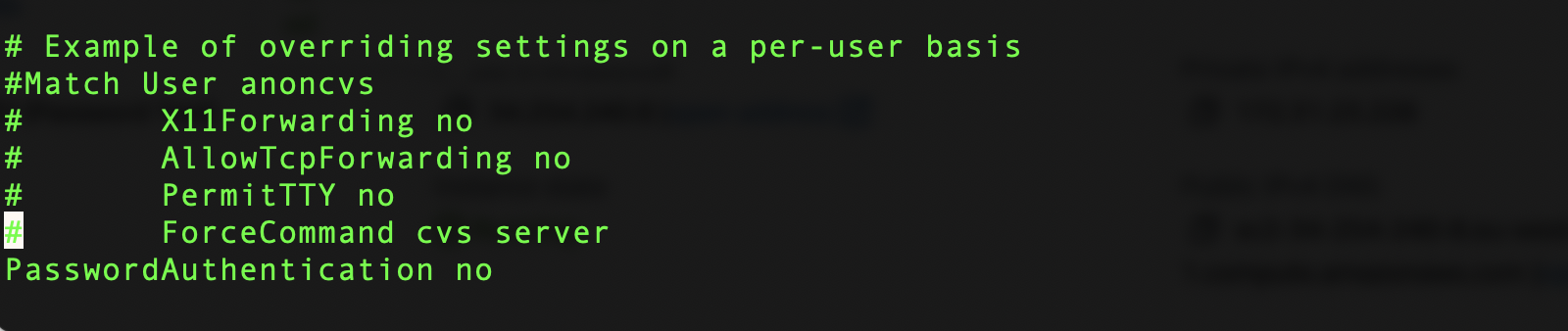
Find the PasswordAuthentication line of the file
Note: the # symbol comments out commands. If a # is in front of PasswordAuthentication then the sshd_config file will not read the command
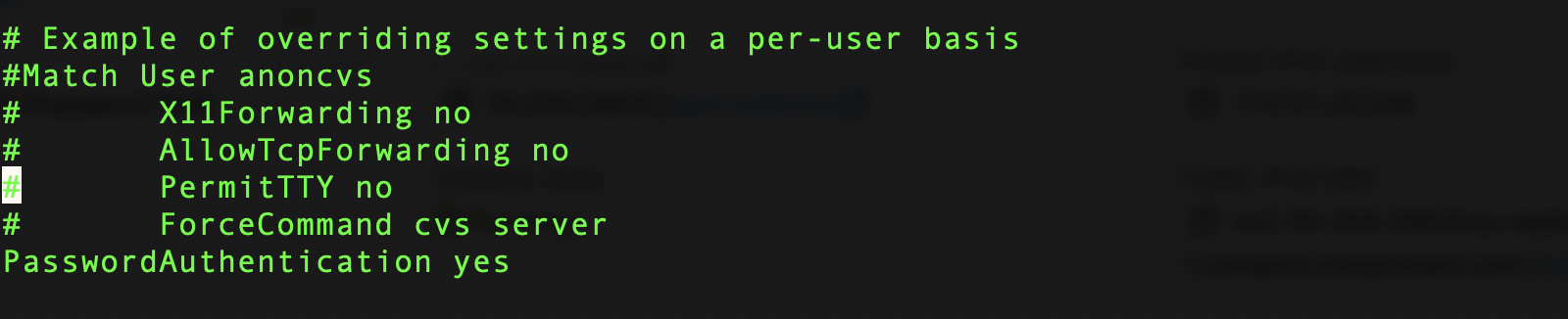
Set the option to yes
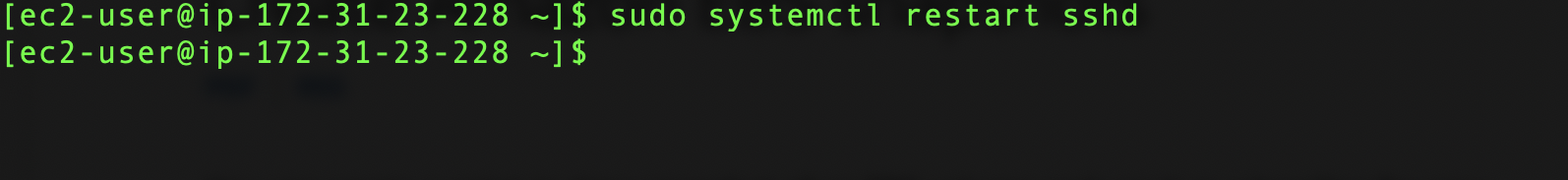
Finally, restart the SSH service
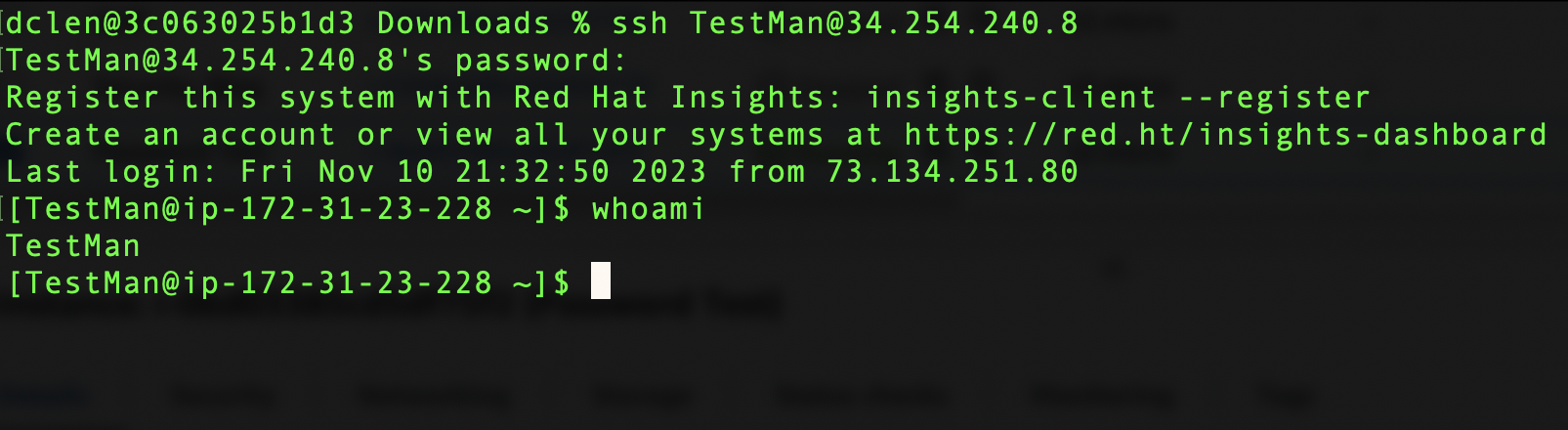
Now you will be able to login to the system using the username and password of your user. For the purpose of this example I made a user with the following command. Be sure to include a secure password!
sudo adduser TestMan
You can change a users password with the following command
sudo password TestMan
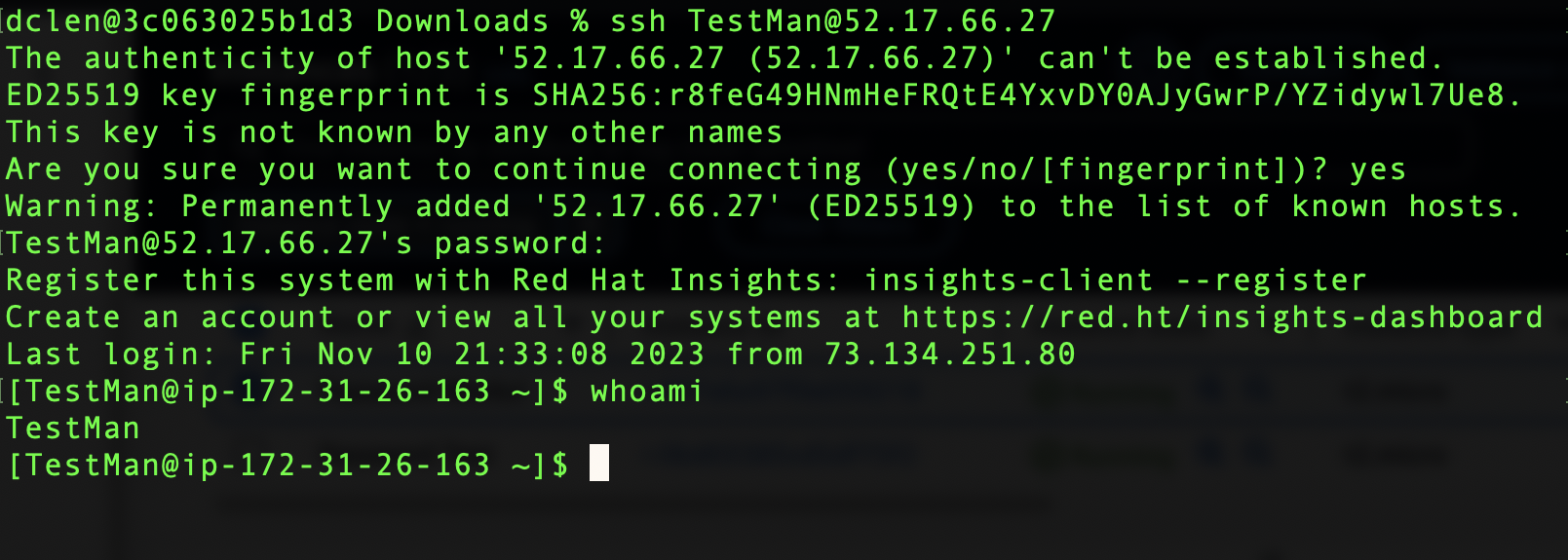
Now we can connect to our instance by using the Username TestMan and the corresponding password
Since Password Based Authentication for SSH is widely regarded as insecure many service providers disable it by default. This is also the case with AMI’s in AWS, which leads to our problem. Let’s observe what happens when we take a snapshot of the instance we enabled Password Authentication on, and then we create a new instance from that snapshot.
Creating and Launching New Instances from Snapshots
The following documentation explains how to create and manage Snapshots in AWS
While this documentation will explain how to create Images as shown below
I started by creating an AMI and Snapshot of my Red Hat 9 server following the steps below
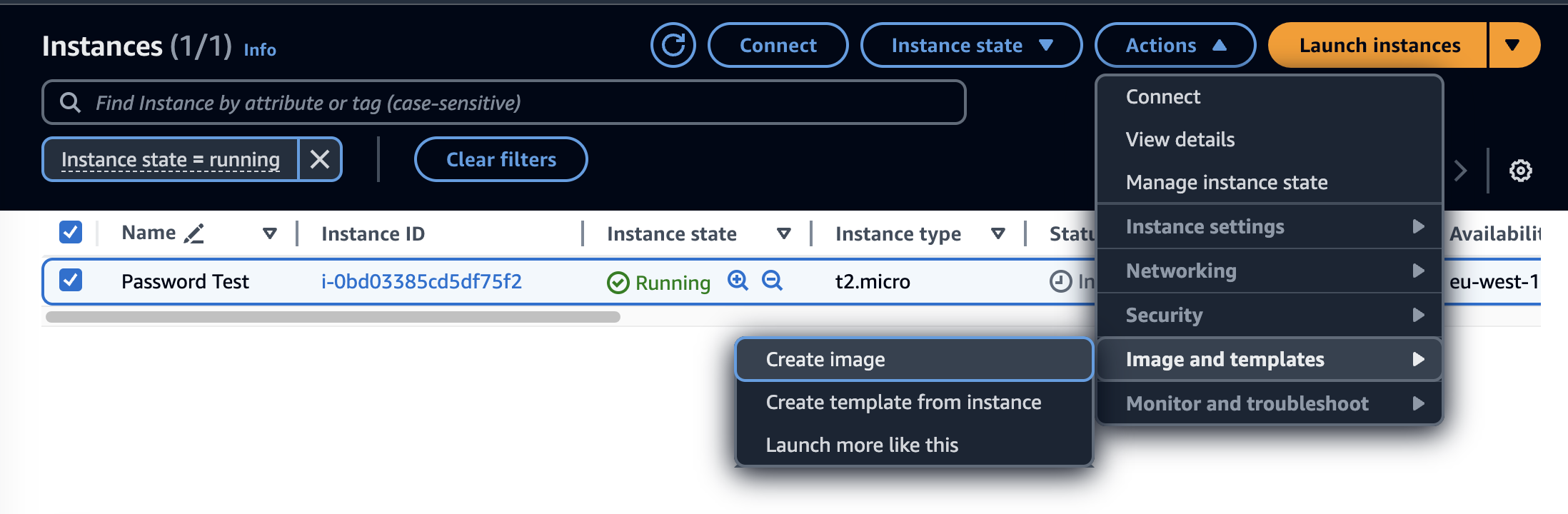
Select the instance, click 'Actions' in the top right.
Under 'Images and Templates' select 'Create Image'
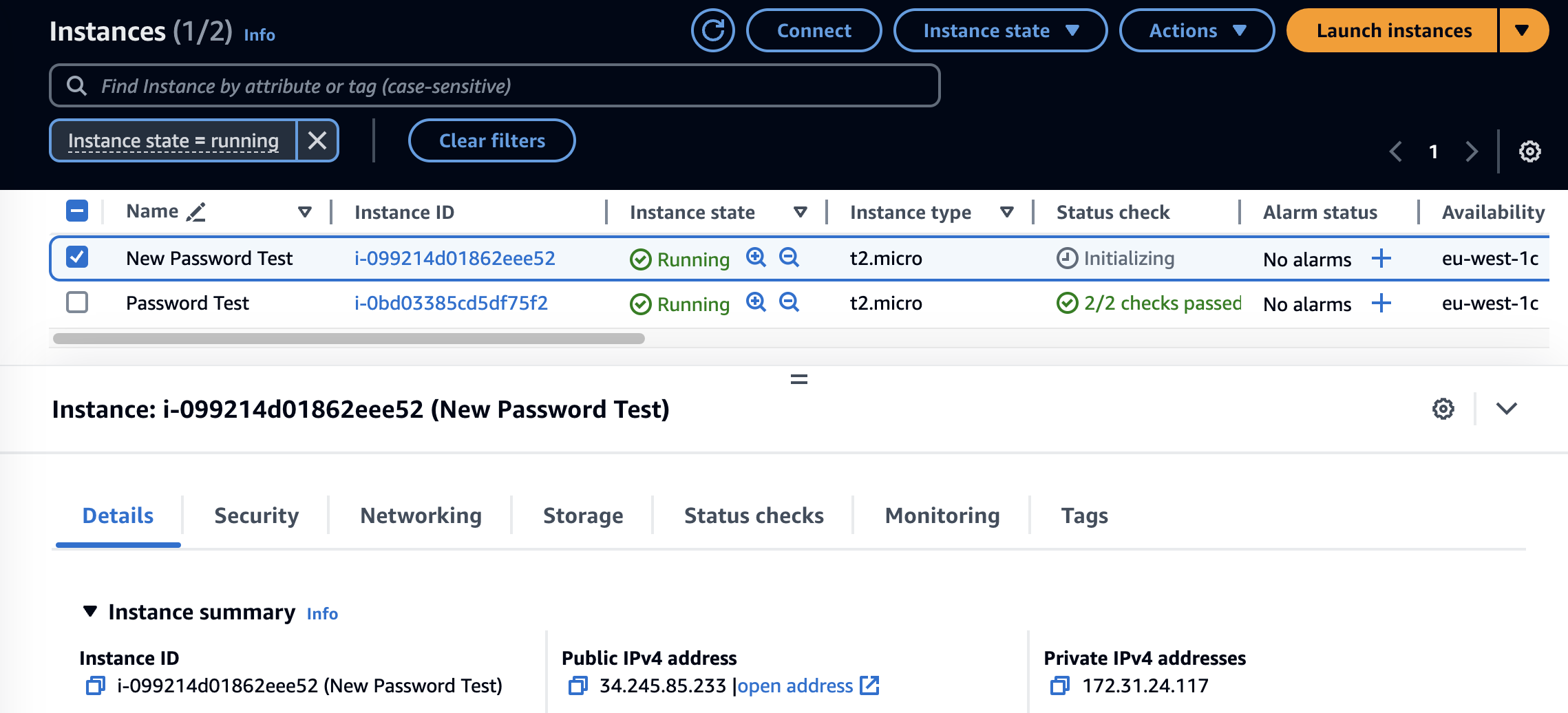
Switch to the AMI tab of the EC2 Console under ‘Images’. Once the AMI is showing as available launch an instance from it. Below we can see my new instance based off the AMI of our first instance, ‘Password Test’
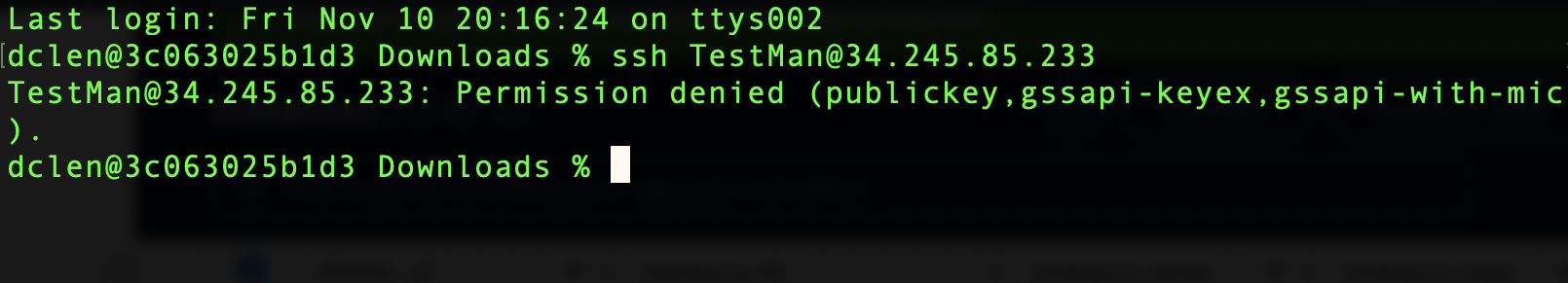
I will now try to connect to the new instance, ‘New Password Test’, with the same username and password that worked on ‘Password Test’
Unfortunately we get Public Key Errors when we attempt to login as TestMan
After connecting to ‘New Password Test’ via Public Key Authentication I reviewed the /etc/ssh/sshd_config file and noticed something interesting.
Our previous changes to set PasswordAuthentication to yes were reversed! Perform a sanity check on your initial instance, in my case ‘Password Test’, and you will see that PasswordAuthentication is still showing as yes.
Why Did This Happen? How Do I Fix This?
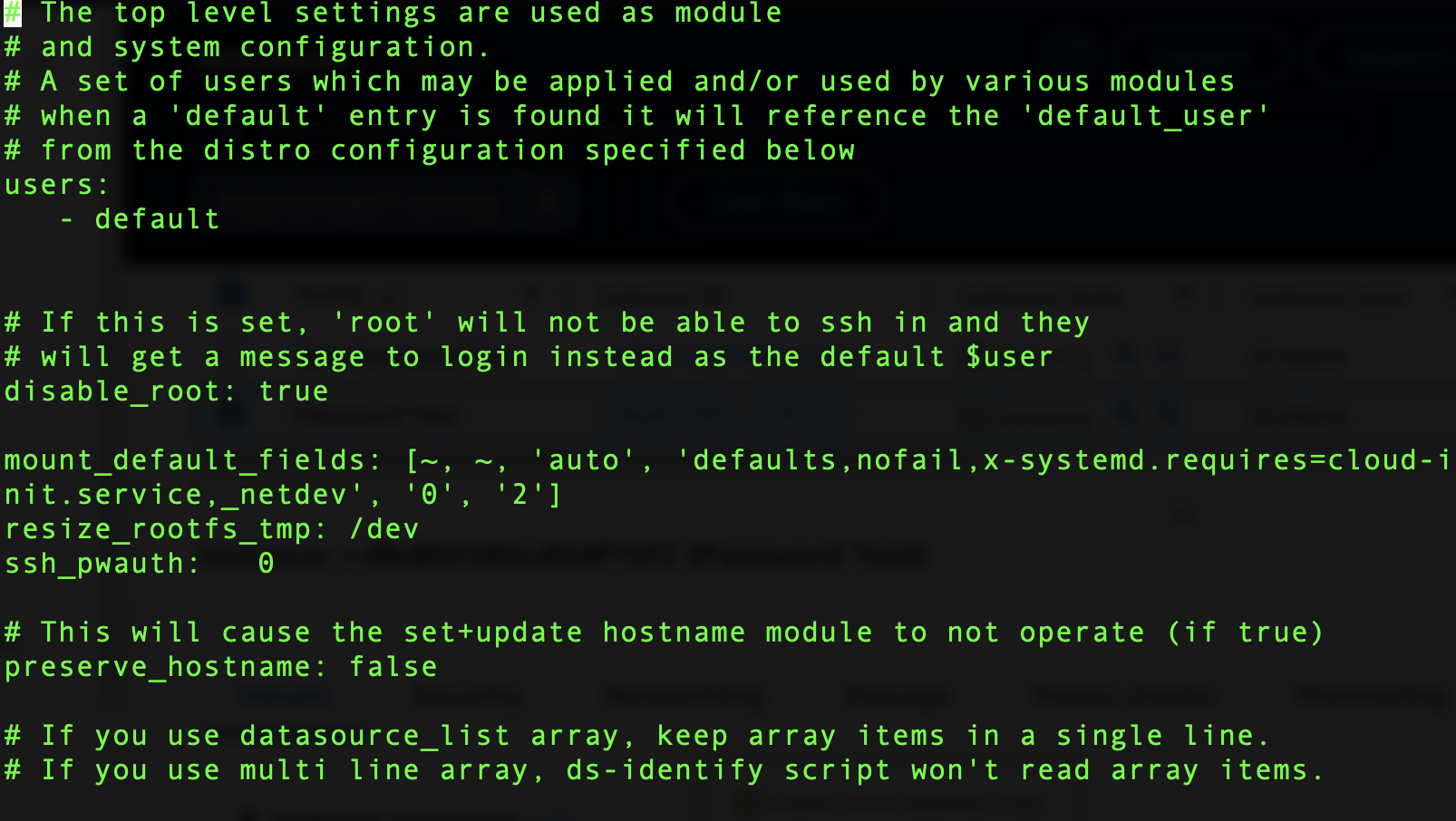
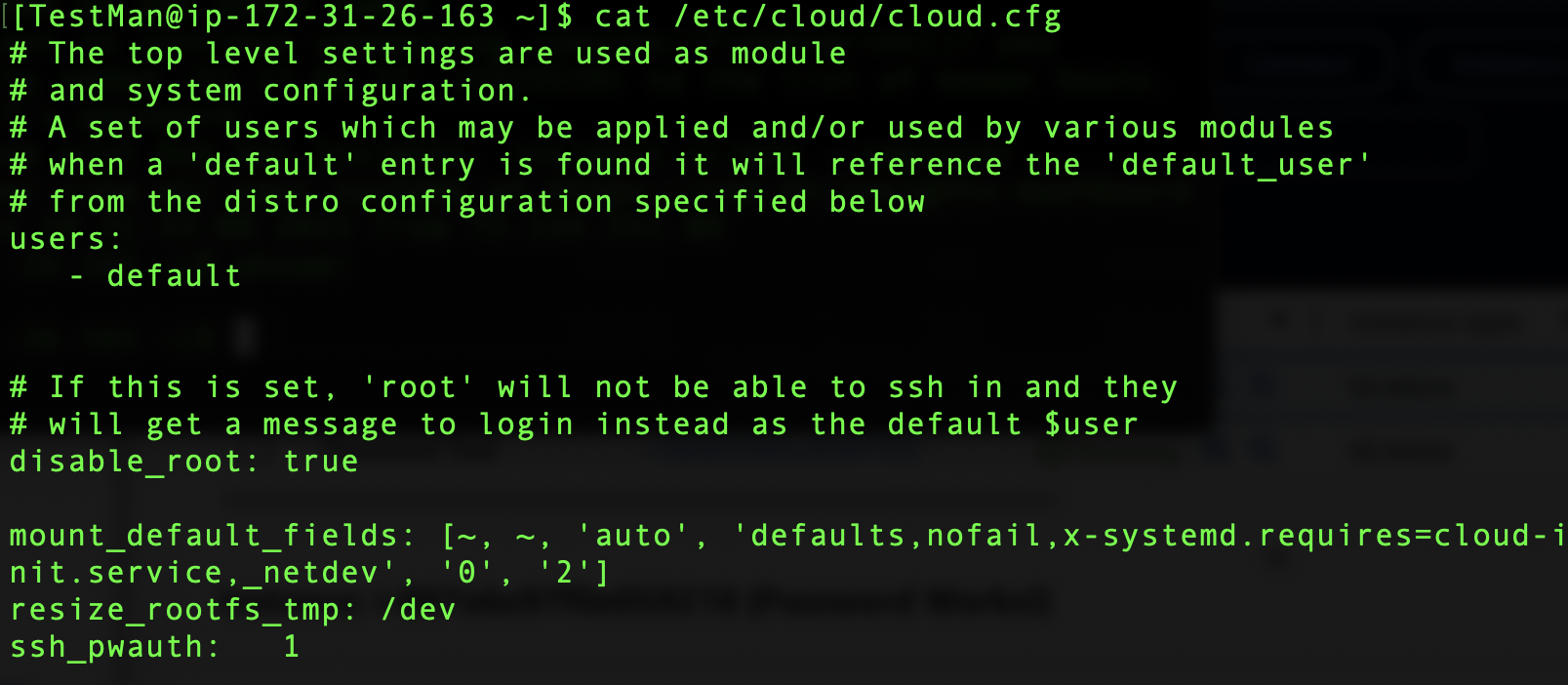
As I mentioned at the start of this article, Password Based Authentication for SSH is very dangerous. Due to this AWS has adjusted their Cloud-init scripts to prevent this behavior by default. Lets review the /etc/cloud/cloud.cfg file for our original instance ‘Password Test’
The setting we want to pay attention to is
ssh_pwauth: 0
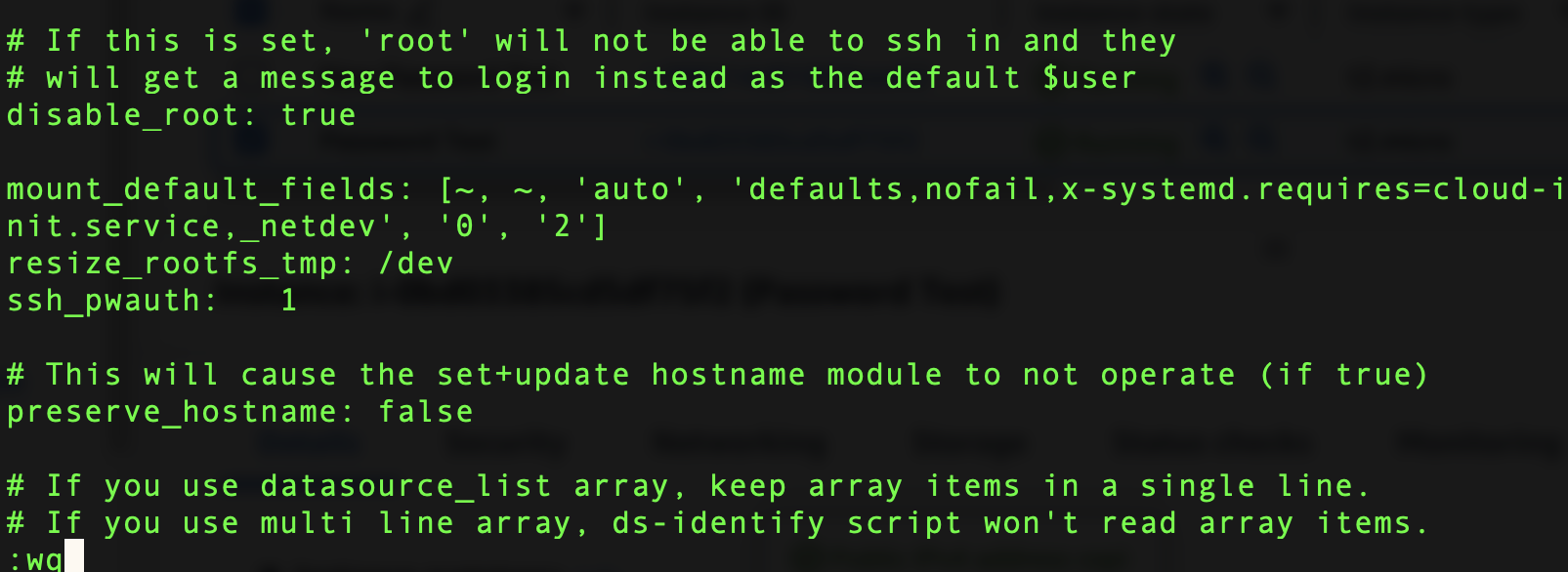
This is what will disable Password Authentication when creating backup Images of an EC2 instance. Despite whatever setting you have configure in /etc/ssh/sshd_config, the cloud.cfg file has ssh_pwauth set to 0 then you will not be able to access your instance via Password Based Authentication. Lets change that and create a new AMI to test our work around. Make the following change in /etc/cloud/cloud.cfg and save the file.
Proceed to create a new image of your instance, in my case ‘Password Test’. Once the new AMI shows as available launch an instance from it. I will try to login with the TestMan user once again.
It works! The previous configuration of the sshd_config file persisted for the image after updating the pwauth setting to 1. As a proof of concept lets take a look at the /etc/cloud/cloud.cfg file for our successful instance.
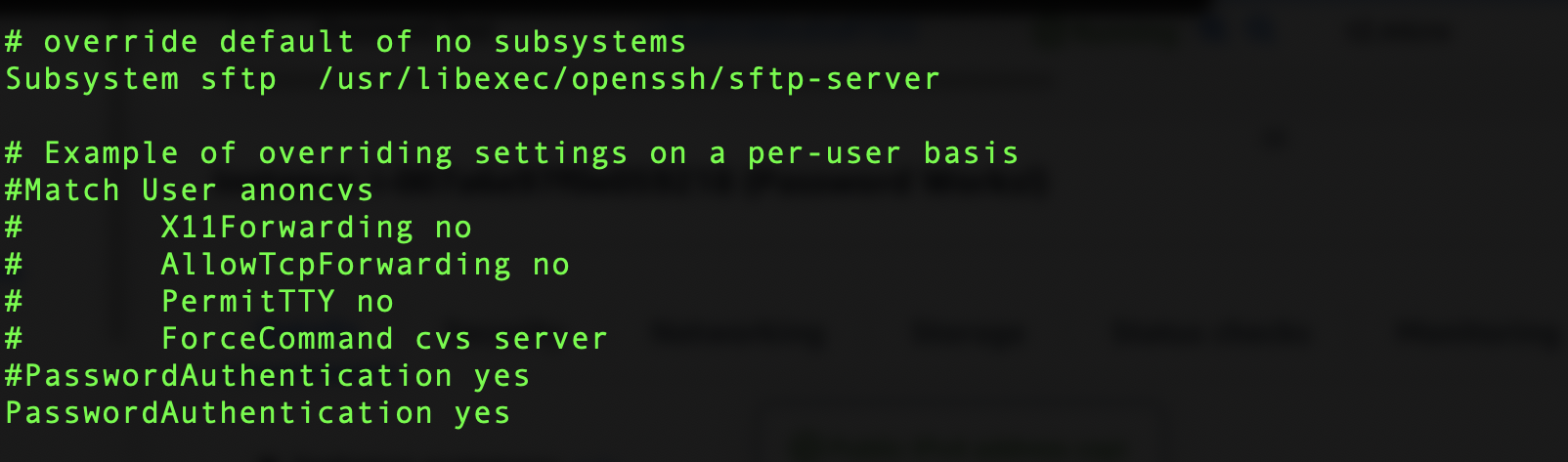
We see that the pwauth is configured properly. Lets review the sshd_config file as well.
The PasswordAuthentication setting remained unchanged, as expected!
Closing Thoughts
Personally, I would never allow Password Based Authentication for SSH on any of my machines. The risk of a threat actor being able to Brute Force into the server is too high. Key-Based Authentication not only enhances security, but it mitigates the risk of password interception. Relying on users to manage and protect their SSH Keys could lead to security risks via negligence. However, allowing users to pick their own passwords is in no way better. At least in my professional opinion.
Regardless, if you are willing to accept the risks that come with Password Based Authentication, then feel free to implement this on AWS. If not, then I hope I was able to showcase something new and interesting for whoever is reading this!